НОВОСТИ МГИМО
НОВОСТИ МИД РОССИИ
Review of Cyberspace of Germany and Russia and Related Issues
Yulia A. Lapotnikova,
School of Governance and Politics, MGIMO University
Abstract:
The article runs about countries’ adaptation with innovations, criminalization of cyberspace and being taken measures against. Germany and Russia are active actors of multilateral international relations. In this regard, the two states are to move with the times and keep up with the world society. The problems of cybercrime have recently gained in importance for every developed countries and also for developing countries involved. This sphere is still not that studied, thus, this research seeks to fill the gap by using about thirty years of data with the focus on current situation to compare the conditions in cyberspace od Russia and Germany. The main objective of the research is to shape a comprehensive image of cybersecurity, cybercrime and developments in this field of the two states and analyze its causal connections for the sake of an ability to make some predictions for the present and future times both.
Key words: cyberspace, cybercrime, CRI 2. index
Main Body
Literature used during the research covers most of the questions posed. As these problems are ‘young’ there are not many comprehensive works, but only distinct articles or data reports of countries’ bodies. The main resources in use were mass media publications of such agencies and journals as Duetsche Welle, RT, RBK, The Guardian, Kaspersky and Group-IB.
The interview with Melissa Hathaway has greatly contributed to this article as well as the work of Siegmunt O.A. ‘Komp’yuternaya prestupnost' v Germanii’, the article of Deryugin R.A. ‘Cybercrime in Russia’. The online map of cyberattacks by Kaspersky turned out to be utmost important and useful for the analysis.
The majormethod used in currentarticle isanalysisof historical perspective and statistics. It provides with the opportunity to consider the topic from all the directions and to drove to reasonable conclusions.
The new information age might be considered from two sides. It is difficult to overestimate the contribution to world development made by technological progress. Over the years more and more countries get an opportunity to have personal devices and become integrated to global network. Where a person is, mobile phone provides an access to the Internet, navigator, online-bank and so on. But these functions make people vulnerable. IT specialists create programs threatening protection of personal data. Everybody can be easily hacked in social networks, for example. Private mail and photographs may become publically accessible. But it is alower level, there are much larger problems.
Intergovernmental relationships have become tense recently. One of the reason is rising IT power of each. Education in this sphere is getting more popular every day, governments pay much attention to theoretic and applied science and ensure funding. At the same time juridical regulation of cyberspace should be also steadily developed so that to avoid incidents and its criminalization. However, it is impossible to prevent all the illegal actions. Here comes a new born term ‘cybercrime’. The topicality of this thesis is based upon ongoing process of day-to-day increasing of these crimes’ frequency.
Two first and foremost premises of its emergence are invention of the computer and the spread of the Internet. Cybercrime can be also both: a one-off act and a set of wrongful acts committed on a certain territory, and considering the second definition the data might be taken into research for a certain period. This type of crime is famous for the fact that, in accordance with country’s getting in in the cyberspace many people immediately see here a strong economic case and try to profit it, thus, become cybercriminals.
This study looks both at the global crisis in the area and at the security situation in two states: Russian Federation and Federal Republic of Germany. There are a number of issues to overcome. The two countries have either some tendencies in common, or several differences. Issues primarily related to legislative regulation of the cyberspace also need to be considered while implementing statistical analysis of cybercrime in Germany and Russia for the period of last 30 years.
The council of Europe signed the Convention on Cybercrime in 2001 in Budapest, which became the first official document of great importance establishing rules of the field. It is identified in the article that there are 4 main kinds of cybercrimes: 1) acts against the confidentiality, integrity and accessibility of computer systems (violations of network security), 2) computer-related fraud, 3) data-related offenses (child pornography, hate crimes) and 4) infringements of copyrightand related rights. Its provisions, however, are not binding.
The countries are empowered to apply any methods in the fight against cybercrime at their own discretion. Its main objective set out in the preamble is to pursue a common criminal policy aimed at the protection of society against cybercrime, especially by adopting appropriate legislation and fostering international co-operation.Germany signed the Convention in 2001 but ratified it only 8 years later. Russia has not joined yet. However, Russia and Germany have some common things in the terms of cyberspaceas it is already mentioned above.
As for Germany, the government also signed and ratified the Additional Protocol to the Convention on cybercrime that criminalizes racist and xenophobic activities carried out through computer systems. In the National Cyber Security Strategy, Germany reaffirmed its commitment to further efforts to harmonize international criminal law through the Budapest Convention. In July 2015, the IT Security Act was adopted in Germany, the purpose of which is to prevent damage to crucial IT systems, such as the computer base of Ministry of the Interior (BSI), telecommunication service providers, components of infrastructure and etc. National legislation is aimed at guaranteed accessibility, authenticity, confidentiality and integrity of cyber security systems and ongoing works and developments in this direction through aforementioned security standards as well as enhanced protection for nationally critical infrastructure elements.
With regard to specific bodies, there are the National Cyber Response Center (Nationales Cyber-Abwehrzentrum, NCAZ) established to respond to incidents and protect data, the National Cyber Security Council seeking to enhance cooperation between public and private sector, the Federal Office of Information Security of the Ministry of the Interior (Bundesamt für Sicherheit in der Informationstechnik, known as BSI) that is responsible for the country's cyber security in general, as well as responsible for the implementation of the accepted strategy.In April 2016, Germany started creating a cyber-command. The Command in Cyber and Information Space (Kommando Cyber und Informationsraum, KCIR), unites all already existing units working in this area, and is also responsible for cyber security, IT (networks), military intelligence, and geo-systems. It is remarkable that BSI was created much earlier (1991) to provide IT security services to the federal government, ICT companies, private and commercial users.
One of recent achievements is an operation against cybercriminal network Avalanche (English avalanche) that was identified and destroyed by German police in cooperation with intelligence agencies of more than forty countries, Europol, the US Department of Justice and the FBI. A huge network of computers being attacked, whose owners did not even suspect anything, was used to provide cybercrimes as a service: customers were offered a “range” of malware distribution, interception of banking data, illegal access to information and much more.
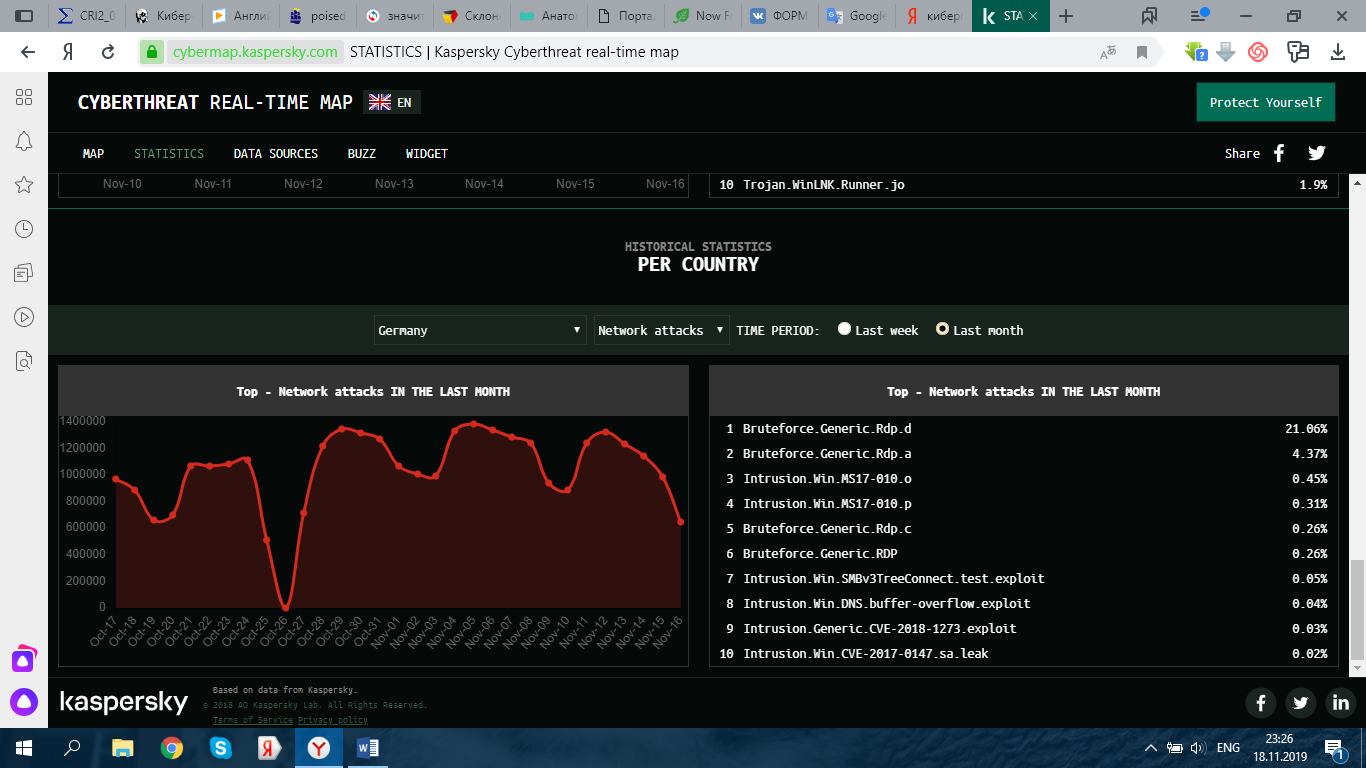
Despite being a leader in development and introduction of ICT technologies, Germany also faces high cybercrime: industrial espionage, intentional violation of critical services as well as other malicious actions in cyberspace. For instance, In 2013, experts claimed that two out of five Internet users in Germany become victims of cybercrimesand a large number of companies and government bodies have suffered fromcyber-attacks.
The Law on Measures Relating to Social Networks that has come into force in 2018 requires large network platforms such as Facebook, Instagram, Twitter and YouTube to takeout “illegal content” recognized under 22 sections of the criminal code. There established the fine in the average amount of 50 million euros.
Nevertheless, given all the above, it should be noticed that it remains unclear whether there are successful initiatives in training judges, prosecutors, lawyers, law enforcement authorities and also other specialists in the country.
The issue of information security places first in the agenda in Germany. Supporting the assertion that prior experiences are important, it is worth appealing to the research called" Cybercrime in the German economy in 2015". It includes an analysis of a data set of telephone survey conducted among 505 companies. The respondents represented by leaders and workers of companies can be divided into two groups: those who have already become victims of computer criminals and those who still manage to avoid it.
The number of companies affected by the activities of cybercriminals increased significantly in 2015 for 40 percent in comparison with 2013 26 percent. Most often financial services companies are main targets for cybercriminals. The total damage done to German business by attacks in the period from 2013 to 2015 is estimated by experts at 54 billion euros. And updated statistics is not yet available that is why it remains only to guess whether it has increased or not. (Deutsche Welle, 2015)
But it is also to be illuminated that Germans are not only victims of cybercriminals, but also actors. Group-IB is an international company specializing on the prevention and investigation of cybercrime and high-tech fraud. It is considered to be the first Russian system, the main idea of which is early warning of cyber threats. Organization’s report 2018 based on statistical data indicates that in the international market the first position was taken by phishers aimed at cloud storage, and not at the financial sector. By the volume of phishing sites in the world. Germany is ranked in this list on the 3rd place. According to a Group-IB report, 73% of all phishing resources fall into the following three categories: cloud storage (28%), financial (26%), and online services (19%).
German government acceptes the fact, that it is essential to provide more training qualified specialists so that to ensure sustainable development of IT researches. Many universities get a good founding for introducing new technologies and incorporating them in the electronic system of the state.
With regard to the second research question, current analysis looks at Russian cyberspace.
The first cybercrime in the USSR occurred in 1983. AvtoVAZ programmer interrupted in the conveyor program for personal reasons, thereby stalled production for three whole days. The plant suffered huge losses. Murat Urtembaev pleaded guilty on his own initiative, but the legislation did not know how to punish a criminal in such cases. The case was widely publicized, and the investigation revealed that Murat was just the first hacker caught, there were many of them.
In 1991 the first interstate cyber attack on US Bank implemented by Russia took place. According the database of the Giats Ministry of Internal Affairs of Russia figures related to the increase in crimes can be traced as follows: 7 crimes in 1997;294 crimes in 1999; 1602 crimes in 2003 and so on.
Although it should be noted that crimes were rarely commited beyond the borders of the state as available information reports. The only exception is financial attacks between states.
It started getting more and more intense in 2013. This year the idea of creating information operationtroops appeared. Russian cyber commands were already formed in 2014.
In the framework of building the information society in Russia the Federation Council has launched the development process of the Russian Cybersecurity Concept. Initially, it was thought as a Strategy, but as the time goes it became clear that it was necessary to cover much more than just an action plan. It requires the creation of terminology that is understandable for Russian citizens, the involvement of many authorities, including the Security Council, federal bodies and ministries.
However, FSB did not accept the draft Concept, and the process was stalled. But on the 5th of December in 2016a published decree of the President of the Russian Federation established the beginning of Concept come to force. To high extent of honesty document informs about vulnerable state of cybercrime in Russia and about the strengthening of cyber risks for the country. It was also claimed that the IT equipment is insufficient in comparison with the latest technologies. (Decree of the President of the Russian Federation of December 5, 2016)
The document places a high premium on the prevention of conflicts caused by foreign control of private national information. Attention is also paid to minimizing the information-psychological pressure on citizens and undermining the patriotic and historical foundations of the state.
Until now none of the legislative acts of the Russian Federation gives a concept with the prefix “cyber”. All the crimes related are described through the adjective ‘computer’.
There are few cybercrimes for political reasons in Russia. A big splash came in 2012 before and during presidential election. The so-called March of the Millions was accompanied by attacks on government websites.
The sensational case of the attack conducted by the IT specialist from Krasnoyarsk, who took out the website of Russian President for more than an hour, caused a huge feedback from all sides: the media, authorities and citizens themselves.
Another spread situation is connected with the mayoral election in Moscow in 2018. During it the Moscow Department of Information Technology recorded 162 thousand attacks on the resources of the Moscow government. The main objective of the attacks was reduced to observing the course of the elections and the casting votes.
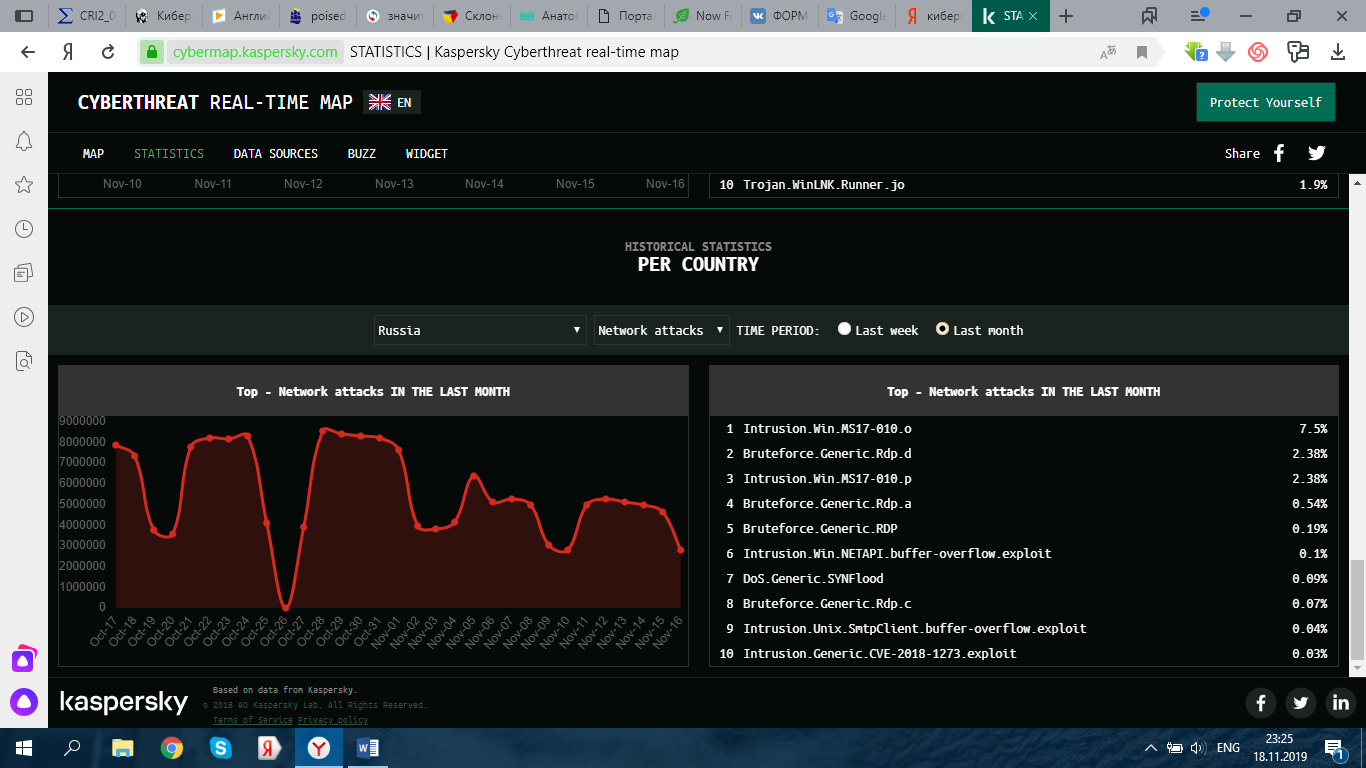
When analyzing the situation in Russia, experts emphasize the threatening vulnerability of the Russian banking system, the damage of which was caused in 2018 in the amount of 2.3 billion rubles. (Group-IB)
Following official statistics, during the period of the first half of 2017 the damage from cybercrimes in Russia amounted to more than 18 million US dollars.
The number of crimes in the field of information and communication technologies increased from 65 949 to 90 587 ones. Their share of the total number of criminal acts recorded in Russia is 4.4%, which is almost every 20th crimes.The most common cybercrimes are illegal access to computer information, the creation, use and distribution of malicious computer programs.
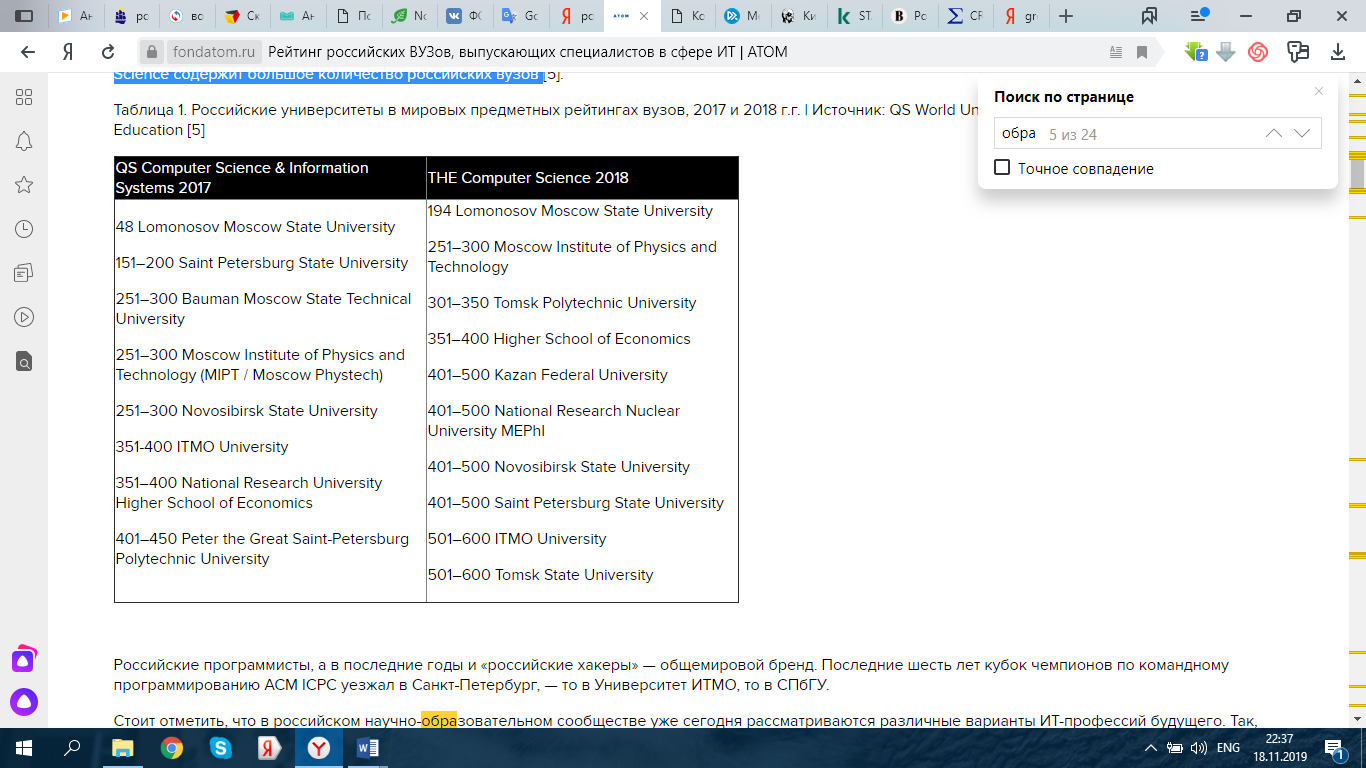
Russian government also realizes the necessity of contributing to education in the sphere of computer technologies. 8 Russian universities in 2017 were included in the international rating QS Computer Science & Information Systems. Moreover, Moscow State University entered the top of 100 world universities in the area studied, taking 48th place. The world rating of The Times Higher Education World University Rankings 2018 in Computer Science that is of high repute all over the world contains even a large number of Russian universities.
With the Digital.Report participating, the report “Cyber Readiness Index 2.0” by Melissa Hathaway, the representative of the Cybersecurity Project at Harvard University, was translated into Russian and released. It highlights the importance of cybersecurity in the country's social and economic development and offers an original methodology for assessing the level of protection of national infrastructure from threats in the cyberspace.
CRI 2.0 Index implies complex methodology that helps country leaders to create conditions for moving towards more stable digital future in competitive and conflict world.
According to CRI 2.0 authors, Germany is on the way to full cyber readiness and now partially corresponds to all the requirements of all seven elements of the Index.
CRI 2.0 founders do not provide any conclusions about situation in Russia, but some comments. Russia is taking measures to get prepared for unexpected cyber crisis. This is only one indicator of the growing maturity of the state.
Taken together these contributions give evidence for differences between the two countries considered. It was stated in the hypothesis that there are both similarities and differences. But such a claim is appeared to be a kind of superstition.
Germany is used to be conservative concerning a comprehensive far-reaching modernization, but nowadays the state takes leading position in the innovations world. Germans have managed to make a great step forward both in improving legislation and advancing technological progress.
Russia is a little behind first and foremost because of the laws, which are notaligned with updated terms. The Russian Federation is still really concentrated on its military power, consequently, most resources go to this field.
Another difference is driving people to modernization. Germans are kept posted with new technologies introduced and something to this row unlike Russians. Citizens here do not know enough about IT; it is a question of civic education.
But the common thing oh these states is achievements in the educational area. As it has been already mentioned above, both Germany and Russia seek to invest a considerable amount of money to the education and training of IT specialists in order to be able to prevent cybercrimes before it is implemented yet.
It could be predicted that Germany will be still one of the leading countries in the sphere of cyber readiness while Russia is gaining its power here. But it is too complicated to foresee the future development of the two countries because then such an analysis definitely requires integration of other countries’ positions in the world.
References
- “Two in Five Internet Users in Germany Hit by Cybercrime in 2013,” eMarketer, May 21, 2014, http://www. emarketer.com/Article/Two-Five-Internet-Users-Germany-Hit-by-Cybercrime-2013/1010845.
- Decree of the President of the Russian Federation of December 5, 2016 No. 646 “On Approving the Doctrine of Information Security of the Russian Federation”
- Deryugin R.A. (2019) Cybercrime in Russia: modern condition and actual problems // Ural Law Institute of the Ministry of the Interior of Russia, Candidate of Law, Ekaterinburg. Pp. 46-49 (In Russ.)
- Federal Ministry of the Interior, “Cyber Security Strategy for Germany,”
- Federal Office for Information Security (2015) “The State of IT Security in Germany 2015,”: 42, https://www.bsi. bund.de/SharedDocs/Downloads/EN/ BSI/Publications/Securitysituation/ IT-Security-Situation-in-Germany-2015. pdf?__blob=publicationFile&v=2.
- https://cybermap.kaspersky.com/stats#country=81&type=ids&period=m
- https://digital.report/
- https://digital.report/kibergotovnost-germanii-2-0-natsionalnaya-strategiya/
- https://potomacinstitute.org/images/CRI/CRI2_0Germany_Russian.pdf
- Melissa Hathaway’s Interview with Arne Schonbohm, Director of BSI (2016), Berlin, Germany
- Siegmunt O.A. (2015) Komp'yuternaya prestupnost' v Germanii [Computer crime in Germany]. Prestupnost' i sotsial'nyy kontrol' vobshchestvepostmoderna // Ch. 1 [Crime and social control in the postmodern society. Part 1]. St.-Petersburg, Alef-Press Publ., Pp. 157-159. (In Russ.)
- Statistics and analytics // https: //mvd.rf [Electronic resource] URL: https: //mvd.rf/Deljatelnost/statistics
- The Federal Government (2014) “Digital Agenda 2014-2017,” 21, www. digitale-agenda.de/DA/Navigation/DE/Home/home.html.
